ISO 27001 is a specification for the management of information security.
- Home
- Certification
- ISO 27001 Information Security
System Certification
- ISO 9001 Certification
- ISO 14001 Certification
- ISO 22000 Certification
- ISO 45001 Certification
- ISO 27001 Certification
- BS ISO 26000 Social Responsibility
- Good Manufacturing Practice (GMP) Certification
- FSSC 22000
- Sedex Members Ethical Trade Audit – SMETA
- Worldwide Responsible Accredited Production – WRAP
- Social Compliance (GCL-SCS:2009)
- C-TPAT Security Audit
Product Certification
- Content Claim Standard (CCS)
- Recycled Claim Standard (RCS)
- Organic Content Standard (OCS)
- Global Recycled Standard (GRS)
- Global Organic Textile Standard (GOTS)
- Global Organic Textile Standard (GOTS: Scope – 4)
- Responsible Down Standard (RDS – Supply Chain Certification)
- Responsible Mohair Standard (RMS – Supply Chain Certification)
- Responsible Wool Standard (RWS – Supply Chain Certification)
- Programme for the Endorsement of Forest Certification (PEFC)
- Canada Organic Regime (COR)
- Zero discharge of hazardous chemical (ZDHC)
- The Forest Stewardship Council® (FSC®)
Inspection and Verification
What is ISO 27001?
ISO 27001 is a specification for the management of information security. It is applicable to all sectors of industry and not confined to just information held on computers. Information may be printed or written on paper, stored electronically, transmitted by post or email, shown on films, or spoken in conversation.
What does information security cover?
- Confidentiality, ensuring that access to information is appropriately authorised
- Integrity, safeguarding the accuracy and completeness of information and processing methods
- Availability, ensuring that authorized users have access to information when they need it
Why apply for ISO 27001 certification?
The objective of ISO 27001 certification is to ensure that there are adequate confidentiality, integrity and availability controls in place to safeguard the information of interested parties. These include clients, employees, trading partners and consumers.
Unprotected systems are vulnerable to an array of threats, including computer-assisted fraud, sabotage and viruses. Such threats can be internal or external, accidental or malicious. Breaches in information security can allow vital information to be accessed, stolen, corrupted or lost.
Information is now globally accepted as being a vital asset for most organisations. Therefore the confidentiality, integrity, and availability of corporate and customer information may be essential to maintain competitive edge, cash-flow, profitability, legal compliance and commercial image.
What are the benefits to your company of ISO 27001 certification?
The ISO 27001 standard is intended to assist with these risks. It is easy to imagine the consequences and damage to a brand or organisation if its information was lost, destroyed, corrupted, burnt, flooded, sabotaged or misused.
An information security management system compliant to ISO 27001 can help you demonstrate to clients and suppliers that you take information security seriously. You will gain a competitive advantage; an ever-growing number of companies require certification to ISO 270001 as a prerequisite for doing business.
You will be able to make a public statement of capability without revealing your security processes. And by ensuring controls are in place, you reduce the risk of security threats and prevent systems from being exploited.
Whatever the media the information takes, or means by which it is shared or stored, the ISO 27001 standard assists in providing a system approach an organisation ensure it is always appropriately protected.
|
|
|
|
|
|
|
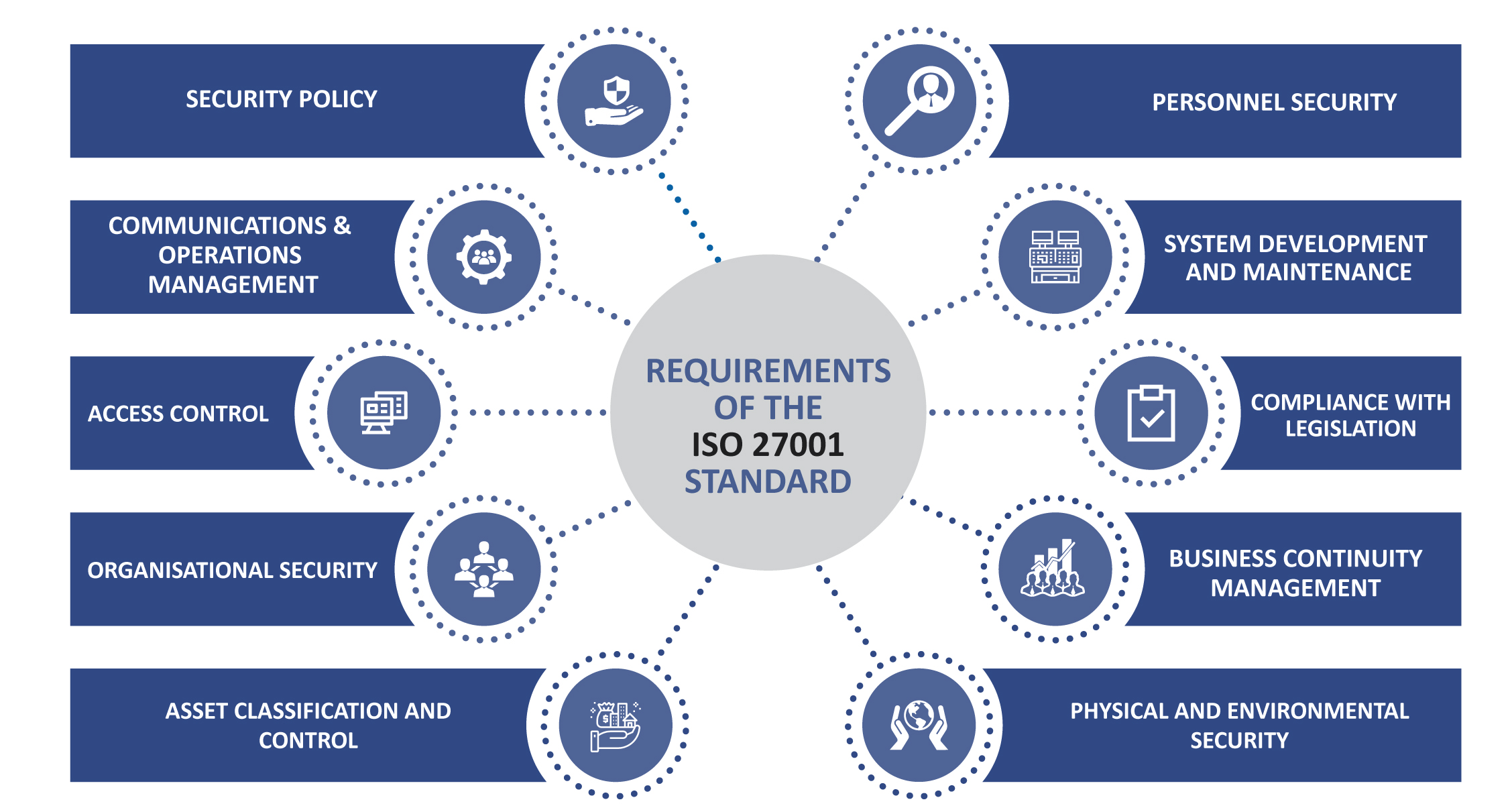
Requirements of the ISO 27001 standard
The main requirements of the standard can be categorised as follows:
|
|
|
|
|
|
|
|
|
|
What is the certification process?
The certification process is in three simple steps:
Application for certification
Complete the on line form for GCL INTL to send a quotation.
Initial Certification Audit
The assessment process is based on a 2 stage approach as follows:
Stage 1 – a basic audit to check whether the organisation is in a state of readiness for the stage 2 audit and involves the following:
|
|
|
|
|
|
Stage 2 – the purpose of this visit is to confirm that the information security management system fully conforms to the requirements of ISO 27001 in practice and involves the following:
|
|
|
|
For more information about ISO 27001 please contact us by phone or email. We will be pleased to assist you.